Our Three Year Journey with ORSHIN
- Maria Chiara Molteni

- 45 minutes ago
- 4 min read
Published on: February 18, 2026
Estimated reading time: 4 minutes
Written by: Maria Chiara Molteni
Edited by: Isabella Donders

As this European project comes to an end, we are proud to present the technical and strategic work finalized in partnership with a robust consortium, encompassing universities (Ku Leuven from Belgium and Eurecom from France), small and medium enterprises (Security Pattern from Italy, Tropic Square from Czech Republic and Texplained from France), and major industry entities (NXP from Germany), perfectly coordinated by Technikon from Austria.
The ORSHIN mission was born from a critical need: how to leverage open source hardware and software for the design of secure connected devices?
In an era of globalized and fragmented supply chains, 'trusted hardware' is no longer a luxury, but it is an absolute necessity for everyone’s security.

Defining the Trusted Life Cycle
One of our primary contributions to ORSHIN was the definition of the Trusted Life Cycle for hardware. We defined the phases a device must undergo, from initial conception to end-of-life, to ensure that security is maintained throughout.
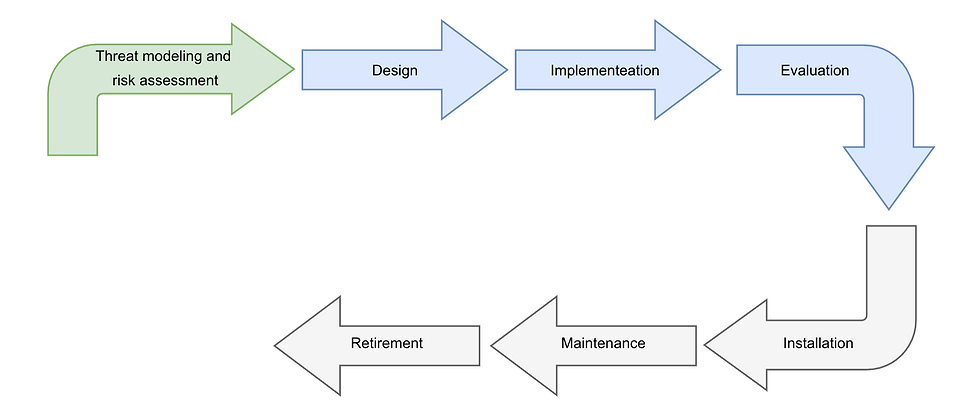
Central to our research was the emphasis on the initial security requirements definition. We recommended a "Security-by-Design" approach, where security objectives are not an afterthought but the very first step of the process. By establishing rigorous requirements at the outset, we ensure that every subsequent stage is aligned with a verifiable root of trust.
This framework provides a clear answer to a complex question: how can we guarantee that open-source hardware remains secure across its entire lifetime?
Pushing the Boundaries of Side-Channel Evaluation
Hardware security is only as strong as its resistance to physical attacks. For this reason, a significant portion of our technical research focused on Side-Channel Evaluation.
As part of this effort, we developed a dedicated tool to determine whether a hardware gadget exhibits side-channel leakage, providing a systematic framework for leakage assessment.
In parallel, we analyzed several custom-designed gadgets implemented on the Tiny Tapeout board using established side-channel evaluation methodologies, enabling us to assess their practical resistance under realistic attack conditions.

Finally, we evaluated the robustness of selected countermeasures applied to the Ascon cryptographic algorithm, carefully analyzing their solidity and effectiveness against side-channel attacks. This combined approach was essential to understanding how theoretical protections hold up when confronted with real-world adversaries.
All the results are collected in the public Deliverable D3.2, which you can read at this link.
Innovation in Communication: The NSCP Protocol
One of our main technical achievements within the project was the design of a new communication protocol: the NSCP (New Secure Channel Protocol).
As a foundational step, we conducted a comprehensive analysis of existing communication protocols and widely adopted cryptographic algorithms. This evaluation allowed us to identify their strengths, limitations, and suitability for constrained embedded environments. In particular, we examined how current solutions address security requirements such as authentication, confidentiality, integrity, and resistance to known attack vectors, while also assessing their computational and hardware overhead.
Recognizing that many existing solutions struggle to balance strong security guarantees with the strict resource constraints of embedded hardware, we designed NSCP specifically to bridge this gap.
The protocol was conceived to provide robust protection without imposing excessive computational, memory, or energy costs on the target architectures explored within ORSHIN.
By combining a thorough evaluation of existing approaches with a targeted, hardware-aware design methodology, NSCP represents a secure and practical solution for next-generation embedded systems.
We have published, together with Vittorio Zaccaria and Joan Bushi from Politecnico di Milano, an article on NSCP titled ‘Design, implementation and validation of NSCP: a New Secure Channel Protocol for hardened IoT’.
All the results about this topic are collected in the public Deliverable D5.2, which you can read at this link.

Sharing Knowledge: Articles, Conferences, and the Summer School
Research achieves its full impact only when it is shared. Throughout the project, we documented our findings in scientific publications and presented our results at several international workshops and conferences, such as the final project workshop we organized during the CHES conference.
At the conclusion of the project, we joined forces with our partners to organize a dedicated Summer School. Over two days of lectures and interactive discussions, we presented our work to engineers and researchers, fostering engaging exchanges and stimulating debate on the future directions of trusted computing.
A Growing Legacy
The ORSHIN project has represented an important milestone in our journey, driving both innovation and meaningful progress. Through this collaboration, we significantly strengthened our capabilities and expertise, built strong strategic partnerships with leading European universities and global industry players, and contributed to advancing a safer and more transparent European digital sovereignty.
We are enthusiastic to build on the experience and insights gained through ORSHIN in our upcoming projects and to continue sharing the results achieved together with our partners.
Learn More about ORSHIN
Visit the official ORSHIN website to discover the impact of this European initiative.
You can also view and download the public deliverables we have made available on this page.
Learn about our participation in all European Projects on our website.




Comments